Steganography is the art of hiding a message / data within a data. Take for example a picture: I can hide/encode a secret message on it by using my Steganographic skills. But it should not be confused with Cryptography which is the art of writing secret codes to obscure a certain message just like the Caesar Cipher or ROT. Combining these two techniques would help you to send your messages securely.
In this tutorial, I will tackle about using two free and open source steganographic tools which are Stepic and Steghide.
Stepic = Python Image Steganography
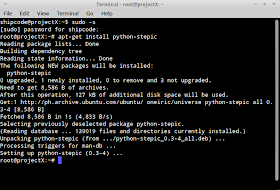
Stepic was coded by Lenny Domnitser and that you can download the tarball on this link. But if you are using Debian based distros like Ubuntu, BackBox, BackTrack, etc. then you just need to type sudo apt-get install python-stepic.
Stepic commands:
-h = shows all the options for using stepic
--version = shows the version of the program
-d = option used for decoding / for showing the message
-e = option used for encoding an image
-i = image file for decoding / encoding (for example rootcon.png)
-o = image name after encoding
-t file to be encoded (for example .txt file)
-d = option used for decoding / for showing the message
-e = option used for encoding an image
-i = image file for decoding / encoding (for example rootcon.png)
-o = image name after encoding
-t file to be encoded (for example .txt file)
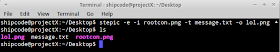
In this example, I have an image named as rootcon.png and a text file named as message.txt. The text file contains a message and that I want to hide it in the image.
To embed message.txt to rootcon.jpg and name it as lol.png you can just type this command in your terminal:
stepic -e -i rootcon.png -t message.txt -o lol.png
Here is now the file that has an embedded data / message on it.
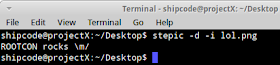
To decode the secret message of the image above, just type this in your terminal:
stepic -d -i lol.png
Steghide = Steganography with Cryptography
Steghide is an application coded in C++ that hides your secret messages / text files in JPEG, BMP, WAV and AU files with the use of steganography. It is similar to stepic but it has cryptographic features which adds encryption to your messages. it asks for a pass-phrase for extracting the hidden data. The current version is 0.5.1 and you can download this awesome tool here. In BackBox Linux, this tool is already pre-installed and under Auditing > Forensic Analysis > File Analysis but you can just use run it using your terminal : steghide arguments <options>.
Important arguments for this tutorial:
embed = embeds data / files
info = display information about a cover or stego file
encinfo = display a list of supported encryption algorithms
help = displays the help menu
Important options for this tutorial:
-cf = select data to be embedded
-ef = select file to be embedded in the data
-sf = select a stego file (file that is already embedded with a data)
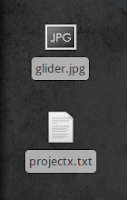
We will use glider.jpg as our image and projectx.txt as our data to be embedded to the image.
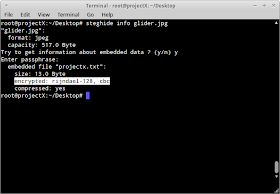
To embed projectx.txt in glider.jpg we use the command : steghide embed -cf glider.jpg -ef projectx.txt
Based on the image above, the program asked me enter a passphrase and that is the protection part. Like I said, steghide uses an encryption of embedded data for protection unlike stepic wherein your embedded files can just be easily decoded using the command : stepic -d -i rootcon.png.
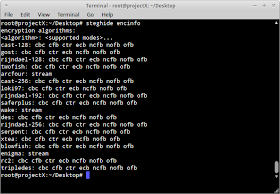
By default the encryption used for the embedded data is Rijndael with 128-bit keys which constitutes the Advanced Encryption Standard or AES and with the use of cipher block chaining mode (cbc) but you can actually use the option -e for selecting encryption parameters. You can issue the command stepic encinfo to display the a complete list of cryptographic algorithms and supported modes you can run for steghide.
And now because we have the embedded data, we can actually check the stego file by using the command info to gather some important data about it.
And yes, it also needs a passphrase for getting the information of the file.
To extract the data (projectx.txt) embedded to the stego file we use the command : steghide extract -sf glider.jpg
And there we have it, our embedded data ;)
There are still other options for steghide, just use the command steghide help to check for embedding options, extracting options, options for the info command, and other arguments.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.