Mutillidae is another free and open source web application for website penetration testing and hacking which was developed by Adrian "Irongeek" Crenshaw and Jeremy Druin. It is designed to be exploitable for it contains vulnerabilities and hints to help a user exploit a certain vulnerability. Ideal for practicing your Web Fu skills like sql injection, cross site scripting, html injection, javascript injection, clickjacking, local file inclusion, authentication bypass methods, remote code execution and many more.
And so for newbies out there. I decided to write a simple guide on how to setup this web application in BackTrack 5. Open your terminal and move to the /var/www where we will be installing the web application: cd /var/www
Download the zip file and extract it:
wget http://www.irongeek.com/mutillidae/mutillidae1.5.zip
unzip mutillidae1.5.zip
Edit the config.inc:
cd mutillidae
gedit config.inc
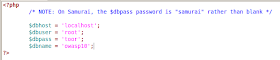
By default the value $dbpass is left blank so we need to put toor which is the default password of BackTrack for connecting to your mysql.
You can also edit the set-up-database.php file so that you can choose what tables, columns and values are to be created or inserted for your database but you can just leave it for the time being. ;)
Now we need to start the necessary services for the web application to run:
service apache2 start
service mysql start
Then open your web browser and point it to 127.0.0.1/mutillidae/ or localhost/mutillidae/.
Now we need to start the necessary services for the web application to run:
service apache2 start
service mysql start
Then open your web browser and point it to 127.0.0.1/mutillidae/ or localhost/mutillidae/.
Next, let's have application setup the database automatically by clicking Core Controls > Setup/Reset the DB at the left side or Setup/Reset the DB at the upperight corner.
The link takes you to 127.0.0.1/mutillidae/set-up-database.php.
The link takes you to 127.0.0.1/mutillidae/set-up-database.php.
If you see no errors then you are ready to play with Mutillidae. You should be able to see the values of accounts table by using basic sql injection to 127.0.0.1/mutillidae/index.php?page=user-info.php.
Enjoy playing with it :)
![localfileinclusion/></a></div>
<br /></div>
<div style=]()
![remotecode+execution/></a></div>
<div class=]()
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Enjoy playing with it :)
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.